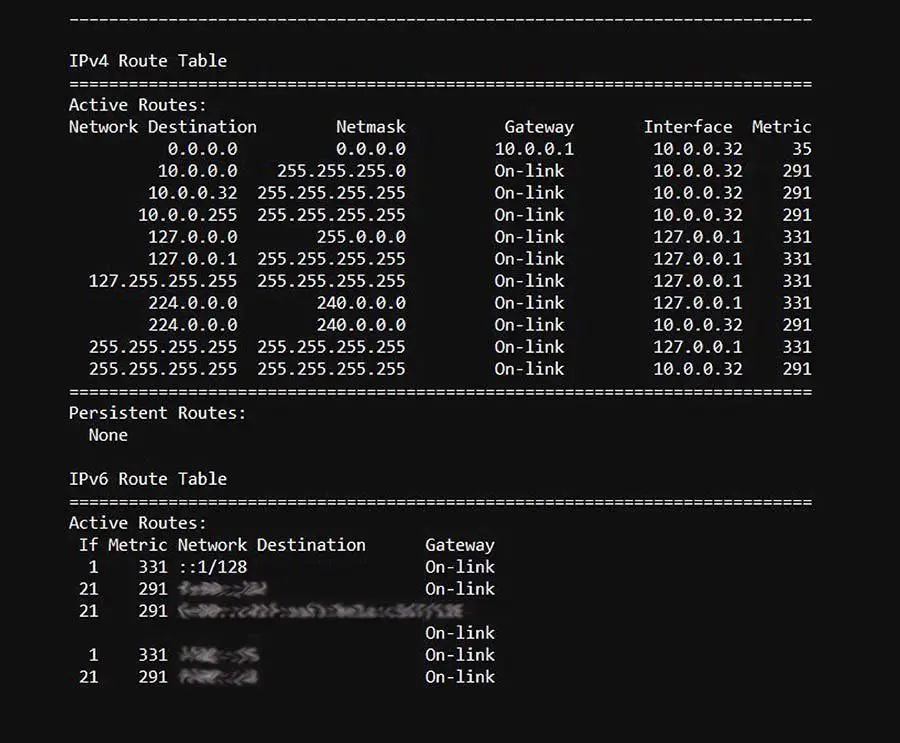
A routing table is a data file in RAM that is used to store route information about directly connected and remote networks. Routers use routing tables to determine where to forward packets so they reach their destination. Routing tables contain information like network addresses, interface details, metrics, and other data needed for routing. They allow routers to look up destination networks and choose the best path to send traffic. So are routing tables really necessary for routers to function? Let’s explore this topic in more detail.
Page Contents
- 1 What is a Routing Table?
- 2 Why are Routing Tables Necessary?
- 3 Key Contents of a Routing Table
- 4 How Routing Tables are Populated
- 5 Key Routing Table Functions
- 6 Why is Frequent Routing Table Lookup Important?
- 7 Impacts of Routing Table Growth
- 8 Alternatives to Traditional Routing Tables
- 9 Routing Table Security Implications
- 10 Conclusion
What is a Routing Table?
A routing table is essentially a map that is used to direct traffic on a network. It is a database that stores network reachability information, including:
- Network ID – The destination network address
- Interface – The outgoing interface a router uses to forward traffic to that network
- Metric – A numeric value used to determine the best route when there are multiple options
- Next Hop – The IP address of the next device to send traffic to enroute to the destination
Routing tables may contain both directly connected networks as well as remote networks. Directly connected routes are added automatically when an interface is configured on the router. Remote networks are ones that can be reached through one or more hops. These routes are added dynamically via routing protocols.
When a router receives a packet, it examines the destination IP address and checks its routing table for the best match. It then forwards the traffic to the appropriate next hop interface. This process allows routers to make decisions on where to send network traffic so it reaches its intended destination.
Why are Routing Tables Necessary?
Routing tables are a fundamental requirement for routers to be able to perform their core function of forwarding traffic between networks. Here are some of the key reasons why routing tables are essential:
To Direct Traffic Flows
The primary purpose of routers is to connect separate networks and ensure packets are forwarded between them. Routing tables provide the map that routers need to make routing decisions and correctly deliver traffic. Without a routing table, a router would not know how to handle packets destined for external networks. It depends on the routing table data to determine where to forward traffic.
To Learn About Remote Networks
Routers discover the existence of remote networks from routing protocols. These routing protocols share network reachability information which is stored in each router’s routing table. Without this intelligence, routers would only know about directly connected networks. Routing tables enable routers to learn about all the networks in the larger topology.
To Build a Forwarding Information Base
Routers make forwarding decisions based on the Forwarding Information Base (FIB). The FIB is generated from the routing table. It contains only the essential information needed to make forwarding choices. The FIB is optimized for fast lookup speed which enables routers to process traffic as quickly as possible. The routing table provides the source data used to populate the FIB.
To Find the Best Routes
Routing tables may contain multiple routes to the same destination. Routers rely on the metric value to determine the optimal route when there are multiple options. Metrics like hop count, bandwidth, delay, load, reliability etc allow routers to select the best path for traffic flows. The metric values in the routing table are essential for this calculation.
To Adapt to Network Changes
Network topologies are rarely static. Links can fail, devices can go offline, configurations can change. Routing protocols update router routing tables in response to topology changes. This allows routers to adapt their forwarding decisions when network conditions change. Routing tables facilitate dynamic recalculation of optimal routes.
Key Contents of a Routing Table
Routing tables include several important categories of data that routers require to make packet forwarding decisions:
Network Prefixes
This refers to the network portion of IP addresses. It can include a full IP address or a subnet in CIDR notation. This allows routers to match destinations to routing table entries.
Outgoing Interfaces
This specifies the router interface used to forward traffic to the destination network. Routers may have multiple paths to a given network.
Next Hops
Next hop addresses indicate the IP address of the next router to send traffic to. Next hops are selected based on the best interface.
Metrics
Metrics provide a value for path cost comparison. Lower metrics identify preferred routes. Metrics can be based on things like hop count, bandwidth, reliability, delay.
Timers
Routing table entries may include timeout timers that delete stale routes or trigger updates. This facilitates recalculation of new optimal paths.
| Network | Mask | Interface | Next Hop | Metric |
|---|---|---|---|---|
| 192.168.1.0 | /24 | GigabitEthernet 0/0 | 0.0.0.0 | 0 |
| 192.168.2.0 | /24 | GigabitEthernet 0/1 | 0.0.0.0 | 0 |
| 192.168.3.0 | /24 | GigabitEthernet 1/0 | 192.168.2.2 | 10 |
How Routing Tables are Populated
Routing tables can be populated in several different ways:
Directly Connected Routes
A directly connected network is any network that is physically attached to the router interface. Direct routes are automatically added to the routing table. Routers insert these default routes when interfaces are configured with IP addresses and subnet masks.
Static Routes
Static routes can be manually configured by a network administrator. These provide a fixed path to a specified destination network. Static routes remain in the routing table until removed or the router is reloaded.
Default Routes
A default route is used to direct any traffic that does not match a more specific route. This provides a gateway of last resort for packets with unknown destinations. Default routes use the subnet mask 0.0.0.0.
Dynamic Routing Protocols
Protocols like OSPF, EIGRP, BGP are used to share network topology information. Routers learn remote network routes from routing protocol messages which are added to the routing table. If the network topology changes, the routing protocols update tables dynamically.
Key Routing Table Functions
Routing tables provide some core functions that allow routers to forward traffic optimally:
Route Lookup
When a packet arrives, the router searches for the destination network in the routing table. The table is indexed for fast lookups. Longest prefix matching is used to pick the most specific route.
Path Selection
If multiple routes to a network exist, the router chooses the best path by comparing route metrics. Lower metrics identify preferred routes.
Packet Switching
The router switches the packet from the ingress interface to the egress interface specified in the matched routing table entry. This enables forwarding to the next hop.
Network Convergence
Routing protocols use the routing tables to determine optimal routes. Any change triggers an update throughout the network which converges on new paths.
Load Balancing
Routes with equal cost metrics allow traffic to be load shared across multiple paths. This provides better utilization of redundant links.
Why is Frequent Routing Table Lookup Important?
Routers make extremely frequent routing decisions – typically thousands of times per second. To avoid congestion, routing table lookups must occur in nanoseconds. Some reasons why fast lookup is critical:
- Minimize packet delay – Quickly move packets between interfaces
- Prevent queue buildup – Look up routes faster than arrival rate
- Maximize throughput – Facilitate high packet handling capacity
- Reduce CPU load – Free resources for other processes
- Support low latency apps – Optimize for real-time traffic
Routers are specialized to provide consistent, rapid route lookups via:
- In-memory routing tables – Avoid slow disk accesses
- FIB optimization – Contains only forwarding info
- ASIC hardware support – Dedicated FIB memory and processing
- Tree bitmap algorithms – Quickly traverse routing table prefixes
- Caching frequently accessed routes – Skip table walk for common routes
Fast routing table lookup enables routers to make forwarding decisions in just a few clock cycles. This is essential to prevent congestion when routing network traffic flows.
Impacts of Routing Table Growth
Modern networks may contain hundreds of thousands or even millions of routes. Several factors contribute to the constant growth in routing table sizes:
- More connected networks – Growth of the Internet expands globally reachable destinations
- Smaller routeable blocks – Route summaries from ISPs advertise smaller netblocks
- IPv4 route fragmentation – Conservation expands routing entries
- IPv6 adoption – Vast IPv6 allocation necessitates more routes
- Policy-driven routing – Traffic engineering and security rules increase paths
Larger routing tables can create several scaling challenges:
- Router memory exhaustion – Routing tables occupy large chunks of RAM
- Slower FIB lookup – Increasing entries take longer to traverse
- Route instability – Frequent changes drive control plane churn
- Forwarding inconsistencies – RIB/FIB synchronization breaks down
- Higher convergence times – Failover and reconvergence takes longer
Router vendors optimize memory management, lookup algorithms, modular architectures, and custom hardware to address these high scalability requirements.
Alternatives to Traditional Routing Tables
Given the routing table growth challenges, alternatives have been developed to improve scaling:
Control Plane and Data Plane Separation
Routers are split into separate control plane and data plane devices. Control plane servers handle routing protocols and build central routing tables. Data plane nodes install optimized forwarding entries.
SDN OpenFlow Networks
SDN controllers program flow table rules directly into OpenFlow switches. This provides more flexible control without routing protocols.
Map-and-Encap Tunneling
Overlay tunneling techniques encapsulate packets with outer IP headers and use endpoint mapping instead of network prefixes for forwarding.
Locator/ID Separation Protocol (LISP)
LISP separates device identities from routing locators to create two namespaces. This improves mobility and multihoming.
MPLS Fast Re-Route
MPLS pre-computes backup paths to bypass failures quickly without reconvergence delays.
Routing Table Security Implications
Routing tables provide significant evidence during forensic investigations. Their contents can reveal details about network topology, data flows, access, and connectivity. However, unauthorized access or modification of routing tables can also pose security risks:
- Route hijacking – Malicious route injection/interception
- Backdoor access – Circumvent protections using surreptitious routes
- Traffic interception – Black hole or redirect flows with false routes
- DoS disruption – Overload routing process with excessive bogus routes
- Reconnaissance – Fingerprint network details through routing table queries
Hardening techniques like routing authentication, route filtering, anti-spoofing, and neighbor limits help secure infrastructure.
Conclusion
Routing tables are a foundational component that enable routers to dynamically interconnect networks and forward traffic optimally based on destination. They provide a mapping database that routers require to make intelligent packet forwarding decisions. Routing tables facilitate automatic route population, dynamic topology discovery, intelligent path selection, fast lookups, load balancing, and network convergence. Continued routing table growth presents scaling challenges that router vendors address through optimized algorithms and custom hardware. While essential to routing operations, routing tables also introduce vulnerabilities that network security controls must mitigate. Given the critical nature of routing, routing tables will continue to serve as a necessary element for enabling efficient network communication.